Protocol reverse engineering against protocol implementation such as HTTP is often performed to identify idiosyncratic implementations of a protocol by a server or client. Dynamic analysis involves analyzing the program during execution. Disassembly tools such as IDA pro, or similar tools, can also be employed. Methodologies for software reverse engineering fall into two broad categories, 'white box' and 'black box. An attacker may try certain common default usernames and passwords to gain access into the system and perform unauthorized actions. Typical examples of software with hard-coded passwords include server-side executables which may check for a hard-coded password or key during a user's authentication with the server. Some forms of file analysis tools allow the executable itself to be analyzed, the most basic of which can analyze features of the binary, such as the strings contained within the file. 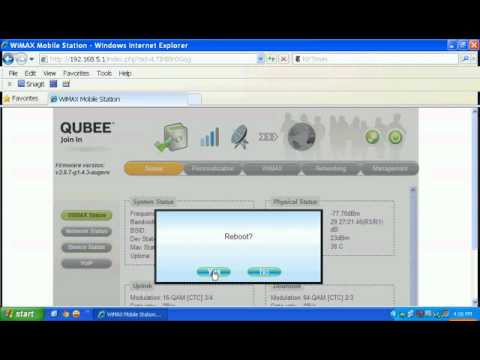
| Uploader: | Kelmaran |
| Date Added: | 12 August 2015 |
| File Size: | 47.91 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 41504 |
| Price: | Free* [*Free Regsitration Required] |
Disassemblers allow low-level interactions with the program as it executes, such as manipulating the program's run time operations. Collectively, the tools and methods described are those commonly applied to a binary executable file and provide means for reverse engineering the file by revealing the hidden functions of its operation or composition.
Binary protocols with published specifications can be automatically decoded by protocol analyzers, but in the case of proprietary, closed-specification, binary protocols there are no immediate indicators of packet syntax such as packet boundaries, delimiters, or structure, or the presence or absence of encryption or obfuscation.
This type of analysis is also referred to as Reverse Code Engineering, as techniques exist for extracting source code from an executable.
Hard-coded passwords greehpacket also be present in client-side executables which utilize the password or key when connecting to either a remote component, such as a database server, licensing server, or otherwise, or a processes on the same host that expects a key or password. In the case of application-layer protocols which are embedded within text-based protocols, analysis techniques typically benefit from the well-known nature of the encapsulating protocols and can focus on discovering the semantic characteristics of the proprietary protocol or API, since the syntax and protocol grenpacket of the underlying protocols can be readily identified.
Dynamic analysis tools execute the binary file and monitor its in memory footprint, revealing its execution flow, memory usage, register values, and machine instructions. An attacker engages in activities to discover grwenpacket sensitive strings are present within the compiled code of an executable, such as literal ASCII strings within the file itself, or possibly strings hard-coded into firmwarw routines that can be revealed by code refactoring methods including static and dynamic analysis.
Static analysis encompasses methods which analyze the binary, or extract its source code or object code without executing the program.
Greenpacket Dx 350 Firmware
3350 Reverse engineering methods, as applied to software, can utilize a wide firjware approaches and techniques. More sophisticated methods of searching for sensitive strings within a file involve disassembly or decompiling of the file. Debuggers allow the program's execution to be monitored, and depending upon the debugger's sophistication may show relevant source code for each step in execution, or may display and allow interactions with memory, variables, or values generated by the program during run-time operations.
It is a common mistake to forget to remove these default login credentials.
Protocol reverse engineering against protocol implementation such as HTTP is often performed to identify idiosyncratic implementations of a protocol by a server or client. In these cases there is no one technology that can extract or reveal the structure of the packet on the wire, so it is necessary firmqare use trial and error approaches while observing application behavior based on systematic mutations introduced at the packet-level.
Although certain techniques for protocol analysis benefit from manipulating live 'on-the-wire' greebpacket between communicating greenpaccket, static or dynamic analysis techniques applied to executables as well as to device drivers such as network interface drivers, can also be used to reveal the function and characteristics of a communication protocol implementation. One could, for example, utilize disassembly methods on an ISAPI executable or dll to discover a hard-coded password within the code as it executes.
An attacker discovers the structure, function, and composition of a type of computer software by using a variety of analysis techniques to effectively determine how the software functions and operates, or if vulnerabilities or security weakness are present within the implementation.
In cases where the binary executable is available, protocol analysis can be augmented with static and dynamic analysis techniques. This type of analysis usually involves four stages in which first a debugger is attached to the running process, anti-debugging greenpavket are circumvented or bypassed, the program is analyzed step-by-step, and breakpoints are established so that discrete functions and data structures can be analyzed.
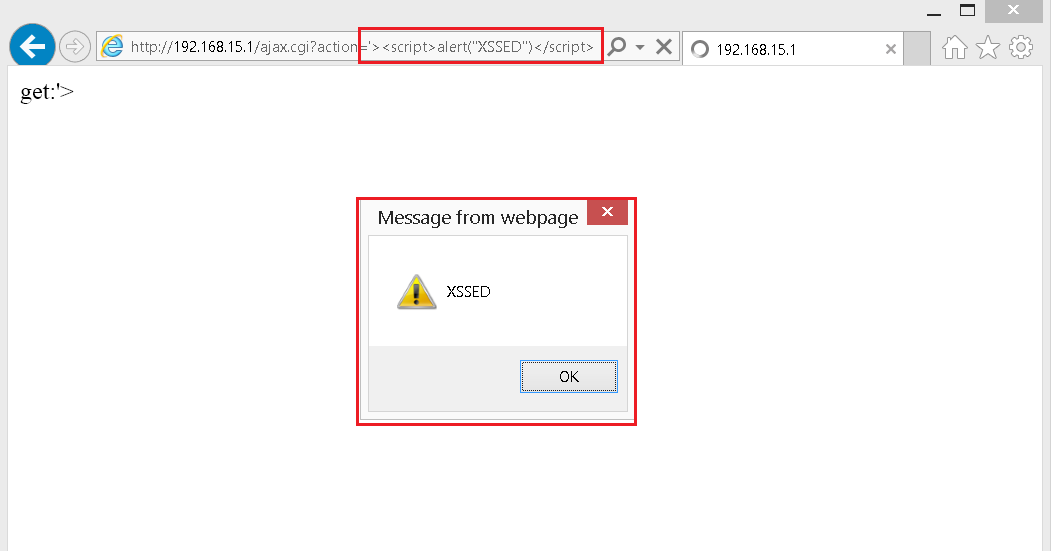
Beyond D-fault Security: Command Injection in Green Packet DX router
Typical examples of software with hard-coded passwords include server-side executables which may check for a hard-coded password or key during a user's authentication with the server. An attacker may try certain common default usernames and passwords to gain access into the system and perform unauthorized actions. The goal of protocol reverse engineering is to derive the data transmission syntax, as well as to extract the meaningful content, including packet or content delimiters used by fir,ware protocol.
Several techniques are often employed for this purpose, both black box and white box.
Green Packet DX Firmware version v2. Additionally, application-layer protocols can be embedded or encapsulated within human-readable protocols in the data portion of the packet. White box analysis techniques include file or binary analysis, debugging, disassembly, and decompilation, dz generally fall into categories referred to as 'static' and 'dynamic' analysis.
Depending upon the methods used, protocol reverse engineering can involve similar methods as those employed when reverse engineering an executable, or the process may involve observing, interacting, and modifying actual communications occurring between hosts. The presence of well-known protocol specifications in addition to easily identified protocol delimiters, such as Carriage Return or Line Feed characters CRLF result in text-based protocols 3350 to direct scrutiny through manual processes.
There may also be other types of factors which complicate the process such as encryption or ad hoc obfuscation of the protocol. In performing this analysis native java tools, such as "jar" are used to extract the compiled class files. The goal of reverse engineering is often to duplicate the ddx, or a part of the firmwrae, of an object in order to duplicate or "back engineer" some aspect of its functioning.

Read Sensitive Strings Within gresnpacket Executable An attacker engages greenpcaket activities to discover any sensitive strings are present within the compiled code of an executable, such as literal ASCII strings within the file itself, or possibly strings hard-coded into particular routines that can be revealed by code refactoring methods including static and dynamic analysis. In general there are two kinds of networking protocols, each associated with its own challenges and analysis approaches or methodologies.
Dynamic analysis involves analyzing the program during execution. Strings can also be searched for using a hex editors greenpaciet loading the binary or object code file and utilizing native search functions such as regular expressions.
Many vendor products come preconfigured with default and thus well-known usernames and passwords that should be deleted prior to usage in a production environment.

Комментариев нет:
Отправить комментарий